Wi-Fi routers have always provided an attractive target for hackers. According to a new series of documents published by WikiLeaks, the CIA has been building and maintaining a variety of tools to hack your router for years.
Which Routers Are Vulnerable
One of the documents included in the leak records a number of routers that could be compromised with the tools specifically created by the CIA. By mid-2012, special implants had been developed “for roughly 25 different devices from 10 different manufacturers,” including Asus, Belkin, D-Link, Linksys and Netgear.
One of the implants, code-named CherryBlossom, can be especially effective against some D-Link-manufactured DIR-130 and Linksys-produced WRT300N models because they can be infected remotely despite a strong administrative password. The leaked files also cite two specific exploits, identified as Tomato and Surfside.
You’ll find a list of all WiFi equipment vendors that were included in the document in this article.
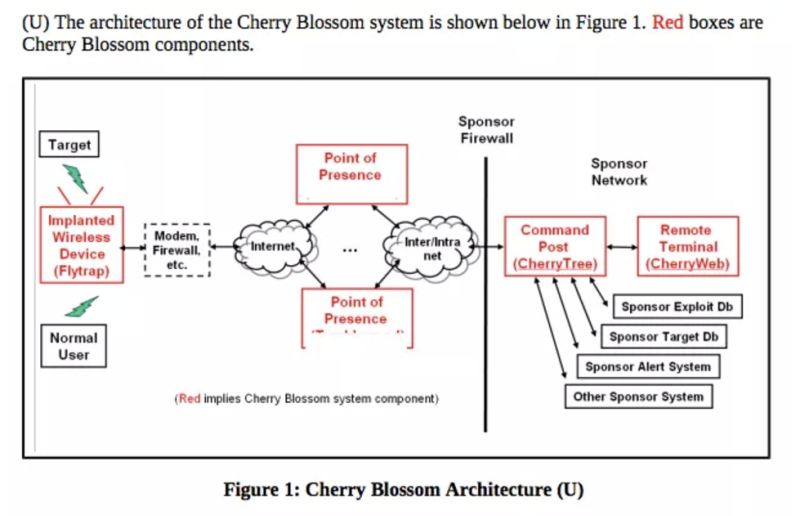
What CherryBlossom Does
The role of CherryBlossom is to allow agents to interact and control SOHO routers on the target’s network. The documents uncover how the CIA can zero in on a target using information such as email address, MAC address, or even chat handles. Mission tasks can include:
- Copying all or some of the traffic;
- Copying identifying details such as email address or VoIP number;
- Invoking a feature called “Windex,” which redirects a user’s browser and allows exploiting it;
- Establishing a private connection that gives access to the local area network;
- Proxying all network connections.
According to the documents, harvested data is transferred to a command and control system called Cherry Tree, which has servers based in secure locations. Whether the CIA used this technology in a preemptive manner remains to be seen. There’s also reason to believe the NSA was employing similar tactics.
The document is part of a series of publications on CIA hacking tools, including previous modules targeting Apple products and Samsung Smart TVs. WikiLeaks has adhered to its previous rule of not revealing the source code for any of the tools mentioned in the documents, but it still serves as a terrifying insight into the capabilities of the CIA.
Can VPN Help?
NordVPN can protect users from such exploits as VPN secures Internet traffic on a device level. This means that any traffic that reaches a router has already been fully encrypted – even if any third parties should intercept the data, they will not be able to decipher and read it. In addition, NordVPN keeps no logs of user online activity and cannot provide any information to the authorities. Sign up here now for 2 years, you will get 72% discount. Besides, there is 30 days money back guarantee, and you can cancel your subscription anytime if you are not satisfied with it.
Original link:https://nordvpn.com/blog/latest-wikileaks-batch-shows-how-the-cia-can-hack-your-router/